确定逆向目标参数
拿取地址、请求body参数,请求头(如果需要)、cookies(如果需要)
分析参数来源,是固定的,还是变动的
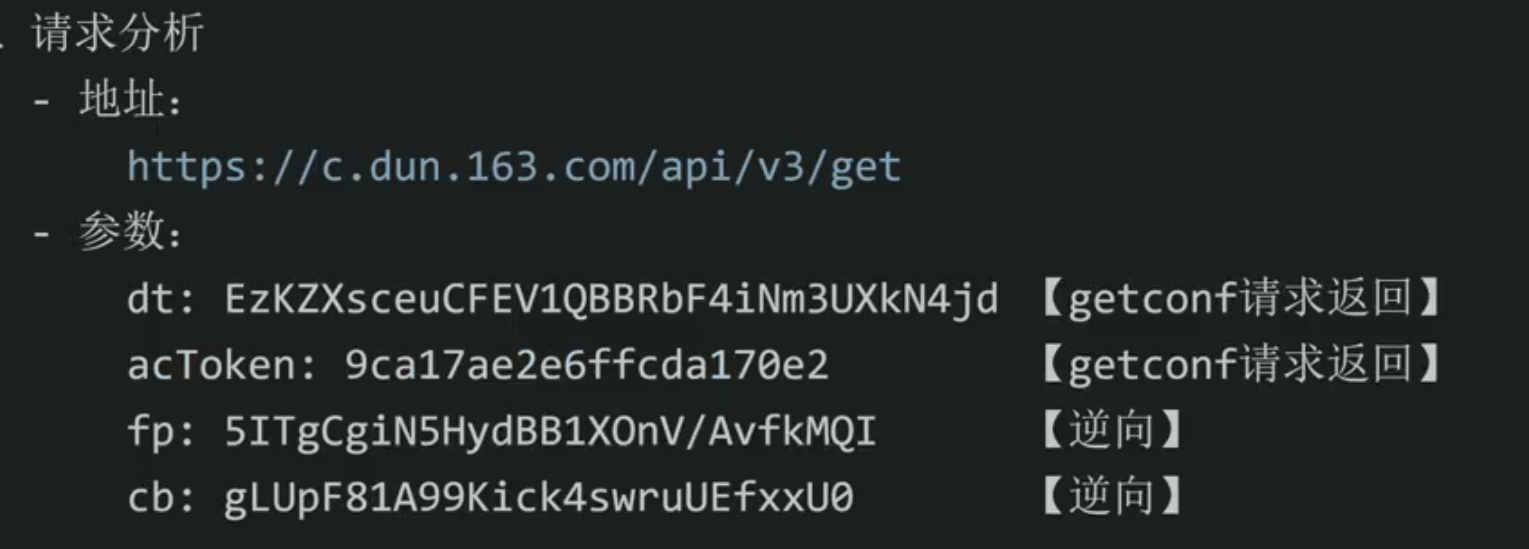
e.g:X盾|获取验证码背景图的接口逆向分析
通过分析,发现需要逆向的有fp和cb参数
分析发现,fp和cb参数所在的js文件是动态的,需要使用动态JS文件处理一下:
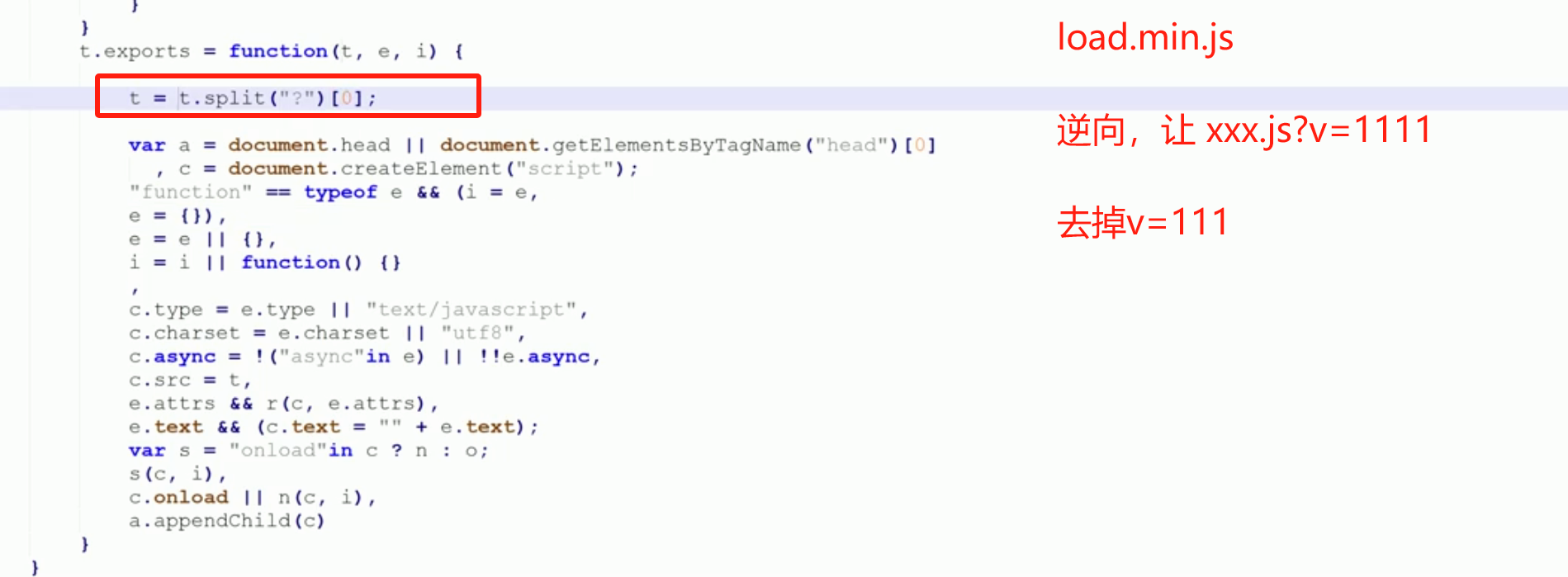
然后使用代理替换解决之。
定位参数
定位到如下直接赋值关键代码:
'fp':wh, #发现需要继续向上。'cb':w1, #简单返回的那种
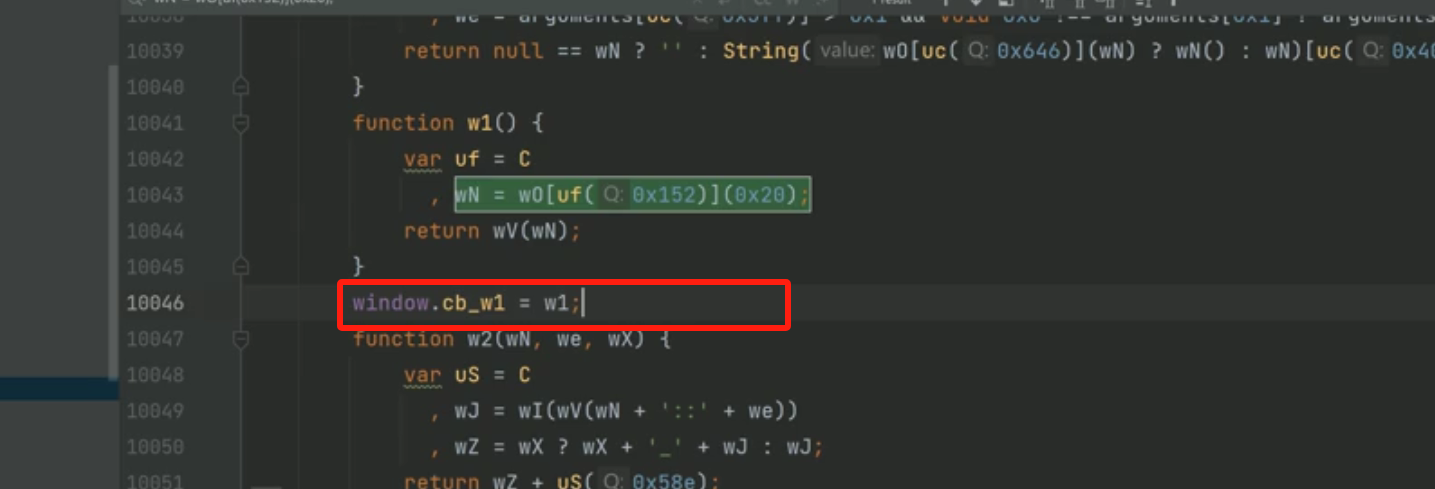
处理cb
拷贝整个JS文件,命名为v1.js
补环境后,写嫁接代码:
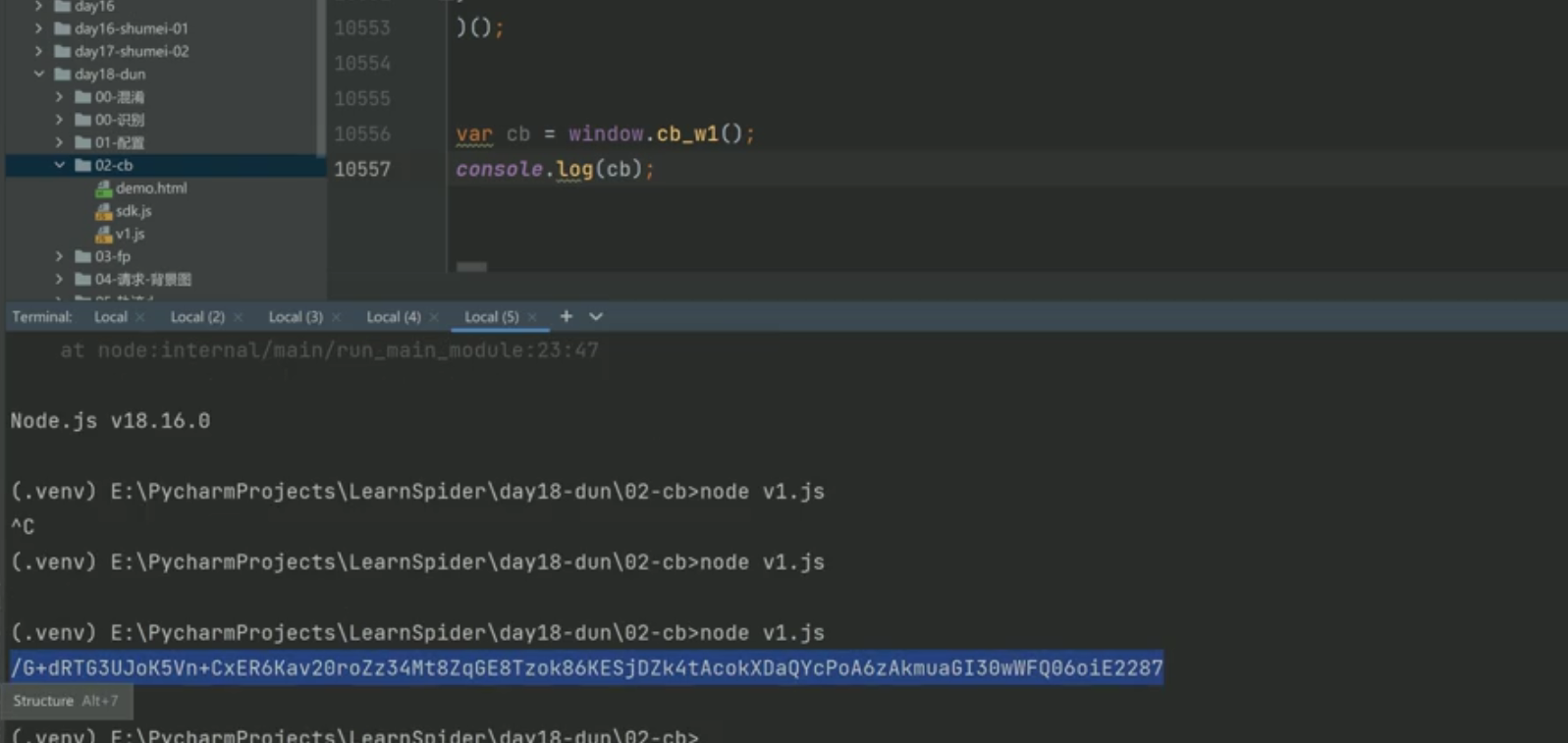
调试看看行不行:
处理fp
定位:
‘fp’:wh,
wh = wJ[‘fingerprint’]
wJ = wN[‘state’]
wN[‘state]=this[‘state’]
一旦涉及到this,就需要看真个对象了
发现对象里有个 initialize
在 initialize 里继续逆向回去
定位到 ‘fingerprint’ : wW
var wW = window[‘gdxidpyhxde’];
然后逆向赋值调试,得知
window[‘gdxidpyhxde’] = wv
发现这个赋值和cb在同一个js文件了,猜测这个js只要执行,就可以自动给window赋值,做个尝试,发现真的可以得到值:
代码整合
结合node.js+py的思路
import jsonimport randomimport subprocessimport requestsimport stringdef cb_fp():res = subprocess.check_output("node sdk.js")char_string = res.decode('utf-8').strip()cb, fp = char_string.strip().split()return cb, fpdef get_conf():callback_string = f"__JSONP_{''.join(random.sample(string.ascii_letters, 7)).lower()}_1"res = requests.get(url="https://c.dun.163.com/api/v2/getconf",params={"referer": "https%3A%2F%2Fdun.163.com%2Ftrial%2Fjigsaw","zoneId": "","id": "07e2387ab53a4d6f930b8d9a9be71bdf","ipv6": "false","runEnv": "10","iv": "3","type": "2","loadVersion": "2.4.0","callback": callback_string},headers={"Referer": "https://dun.163.com/","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36",},)res.close()res_string = res.text.strip(f"{callback_string}(").strip(");")res_dict = json.loads(res_string)dt = res_dict['data']['dt']ac_bid = res_dict['data']['ac']['bid']ac_token = res_dict['data']['ac']['token']return dt, ac_bid, ac_tokendef get(dt, ac_bid, ac_token, cb, fp):callback_string = f"__JSONP_{''.join(random.sample(string.ascii_letters, 7)).lower()}_1"res = requests.get(url="https://c.dun.163.com/api/v3/get",params={"referer": "https%3A%2F%2Fdun.163.com%2Ftrial%2Fjigsaw","zoneId": "CN31","dt": dt,"acToken": ac_token,"id": ac_bid,"fp": fp,"https": "true","type": "2","version": "2.25.0","dpr": "2","dev": "1","cb": cb,"ipv6": "false","runEnv": "10","group": "","scene": "","lang": "zh-CN","sdkVersion": "undefined","iv": "3","width": "320","audio": "false","sizeType": "10","smsVersion": "v3","token": "","callback": callback_string},headers={# "Accept-Language": "zh-CN,zh;q=0.9","Referer": "https://dun.163.com/","User-Agent": "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/119.0.0.0 Safari/537.36",},)res.close()res_string = res.text.strip(f"{callback_string}(").strip(");")res_dict = json.loads(res_string)print(res_dict)def run():# get_conf请求dt, ac_bid, ac_token = get_conf()# get请求cb, fp = cb_fp()get(dt, ac_bid, ac_token, cb, fp)if __name__ == '__main__':run()
